Whispered Closed-circuit Television Secrets
페이지 정보

본문
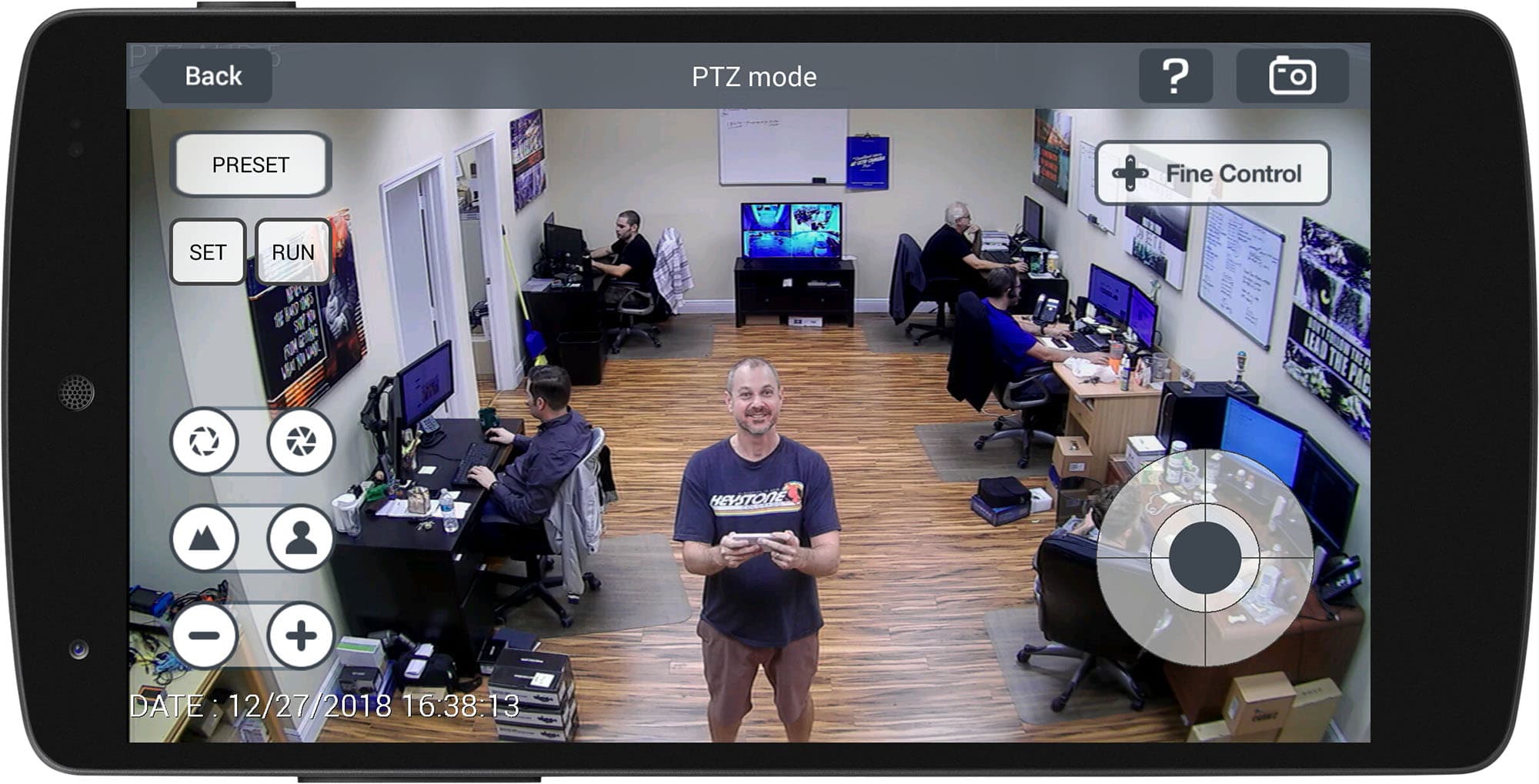 In some particular circumstances, the whole destruction of the compromised system is favored, as it could occur that not all of the compromised resources are detected. Utilizing units and strategies comparable to dongles, trusted platform modules, intrusion-conscious instances, drive locks, disabling USB ports, and cell-enabled access may be thought-about extra secure due to the physical entry (or refined backdoor entry) required in an effort to be compromised. Trusted platform modules (TPMs) safe gadgets by integrating cryptographic capabilities onto entry devices, by means of using microprocessors, or so-referred to as computers-on-a-chip. Constructed-in capabilities similar to Bluetooth, the newer Bluetooth low power (LE), near-area communication (NFC) on non-iOS gadgets and biometric validation resembling thumbprint readers, in addition to QR code reader software designed for cellular devices, provide new, secure methods for cellphones to connect with access control systems. They can be applied as software program running on the machine, hooking into the community stack (or, in the case of most UNIX-primarily based operating techniques reminiscent of Linux, built into the operating system kernel) to supply actual-time filtering and blocking. Another implementation is a so-called physical firewall, which consists of a separate machine filtering community traffic.
In some particular circumstances, the whole destruction of the compromised system is favored, as it could occur that not all of the compromised resources are detected. Utilizing units and strategies comparable to dongles, trusted platform modules, intrusion-conscious instances, drive locks, disabling USB ports, and cell-enabled access may be thought-about extra secure due to the physical entry (or refined backdoor entry) required in an effort to be compromised. Trusted platform modules (TPMs) safe gadgets by integrating cryptographic capabilities onto entry devices, by means of using microprocessors, or so-referred to as computers-on-a-chip. Constructed-in capabilities similar to Bluetooth, the newer Bluetooth low power (LE), near-area communication (NFC) on non-iOS gadgets and biometric validation resembling thumbprint readers, in addition to QR code reader software designed for cellular devices, provide new, secure methods for cellphones to connect with access control systems. They can be applied as software program running on the machine, hooking into the community stack (or, in the case of most UNIX-primarily based operating techniques reminiscent of Linux, built into the operating system kernel) to supply actual-time filtering and blocking. Another implementation is a so-called physical firewall, which consists of a separate machine filtering community traffic.
The configuration required using devoted lanes, drawing criticism from motorists who believed that it exacerbated traffic because of the lack of traffic lanes. Additionally, Rai operates a dedicated visitors information station closely focusing on motorway viability which trasmits on the fastened frequency of 103.Three FM , Rai Isoradio. Forty-four individuals had been injured by the bomb and News of the World photographer Edward Henty was killed after ignoring police warnings and dashing to the scene. It is feasible to scale back an attacker's possibilities by keeping techniques updated with safety patches and updates and by hiring folks with expertise in security. Past vulnerability scanning, many organizations contract outside safety auditors to run regular penetration checks in opposition to their systems to determine vulnerabilities. While sharia legislation, Islamic studies, and Islamic banking could be taught on the campus, there are no verifiable claims that the campus will likely be run by, or will solely train, Sharia law. The video surveillance cameras will even be made use of in workplaces for retaining a watch across the personnel in addition to their carry out schedules. Most of these cameras are noted for their fantastic options that they have. Content h as been generated with GSA Cont en t Generator DEMO!
The movie tells the story of a young digital map-making surveyor, working for a digital mapping firm, who in his spare time helps install CCTV cameras. A few of the popular dwelling safety techniques Gold Coast embrace - the fireplace alarm, the smoke detector, CCTV cameras, and video doorbell, sensible lighting methods. Closed-circuit digital photography (CCDP) is extra suited to capturing and saving recorded images, whereas closed-circuit television (CCTV) is extra suitable for dwell-monitoring functions. Each of these is coated in additional detail beneath. These systems are more reliable and safe. These are systems which have achieved certification from an external safety-auditing group, the most popular evaluations are Common Standards (CC). Mobile-enabled access units are rising in recognition because of the ubiquitous nature of cell phones. IOMMUs allow for hardware-based sandboxing of parts in cellular and desktop computers by using direct reminiscence entry protections. Response is necessarily outlined by the assessed safety requirements of an individual system and will cowl the vary from easy improve of protections to notification of legal authorities, counter-attacks, and the like. Chances are you'll go for any of the dependable programs like the ADT Dwelling Security. CATV operators may choose to watch their networks for leakage to forestall ingress.
 Another safety utility for dongles is to use them for accessing internet-based mostly content corresponding to cloud software program or Virtual Personal Networks (VPNs). Ahead web proxy solutions can prevent the shopper to visit malicious net pages and inspect the content material earlier than downloading to the consumer machines. In addition, a USB dongle will be configured to lock or unlock a pc. Using secure working techniques is a good way of making certain computer safety. Here we explained the most effective eight dwelling safety techniques for your private home. At Base Techniques, we truly consider in distinctive service and value-for-cash and have strived to the perfect in our trade for years. Government Yuan due to the difficult political environment on account of persistent boycott by opposition parties over several financial insurance policies previously 1.5 years. To ensure that these instruments to be effective, they have to be stored updated with every new replace the vendor launch. Here's more about Brandedpoetry look at our own webpage. In order to ensure ample safety, the confidentiality, integrity and availability of a network, higher known as the CIA triad, have to be protected and is taken into account the inspiration to info safety.
Another safety utility for dongles is to use them for accessing internet-based mostly content corresponding to cloud software program or Virtual Personal Networks (VPNs). Ahead web proxy solutions can prevent the shopper to visit malicious net pages and inspect the content material earlier than downloading to the consumer machines. In addition, a USB dongle will be configured to lock or unlock a pc. Using secure working techniques is a good way of making certain computer safety. Here we explained the most effective eight dwelling safety techniques for your private home. At Base Techniques, we truly consider in distinctive service and value-for-cash and have strived to the perfect in our trade for years. Government Yuan due to the difficult political environment on account of persistent boycott by opposition parties over several financial insurance policies previously 1.5 years. To ensure that these instruments to be effective, they have to be stored updated with every new replace the vendor launch. Here's more about Brandedpoetry look at our own webpage. In order to ensure ample safety, the confidentiality, integrity and availability of a network, higher known as the CIA triad, have to be protected and is taken into account the inspiration to info safety.
- 이전글### Network Gear A Comprehensive Gu 25.03.18
- 다음글مقدمة ابن خلدون - الجزء الرابع 25.03.18
댓글목록
등록된 댓글이 없습니다.

